August 25th, 2021 by Admin
There’s no doubt that enterprises today, more than ever, need effective cybersecurity strategies. However a sound strategy is not in and of itself a guarantee of success. There are several ingredients that are necessary for a cybersecurity program to be successful. This chapter will describe what a cybersecurity strategy looks like and each of the necessary ingredients for success in detail.
August 25th, 2021 by Admin
Are we good? This question should give a security team pause. Where do they begin to explain the complexities and nuances of the risks posed by cyber threats? What does “good” mean to an analyst, SOC manager, or CISO? The executive often only wants a yes or no. She may not have the time to pick apart anything more complicated.
August 25th, 2021 by Admin
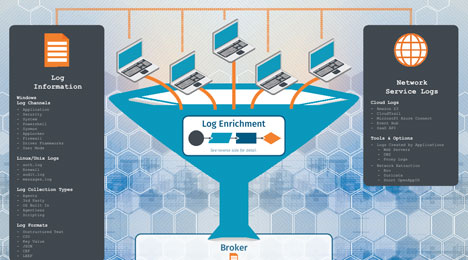
Gathering intelligence and log evidence to support an investigation often requires having an intimate knowledge of the details that may be available across a vast array of log sets and data sources. The analysts’ awareness of what log data is available and where it is stored increases readiness for incident response.
August 25th, 2021 by Admin
Security operations aren’t suffering from a “big data” problem – but rather a “data analysis” problem. A SIEM can be an incredibly valuable tool for the SOC when implemented correctly. Leverage the Log Lifecycle Poster to add context and enrich data to achieve actionable intelligence – enabling detection techniques that do not exist in your environment today.
August 25th, 2021 by Admin
A lot of enterprise networks are under attack or they already have been attacked by the adversaries. Red teamers or attackers tend to compromise the environments with new ways and rely on legitimate tools with sophisticated techniques based on their skill levels. On the other hand, the job of the blue teamers becomes more challenging and difficult as the attacker only needs to be successful once to gain access. (more…)
Categories
Disclaimer
Unless otherwise indicated, Copyrights and Intellectual Property Rights of the documents, reports in this section of the website are under ownership of the original authors. Readers and Users of the information in the form of documents, reports and requested to comply with More..